Find out how to avoid falling into phising
Phishing: a click makes the difference
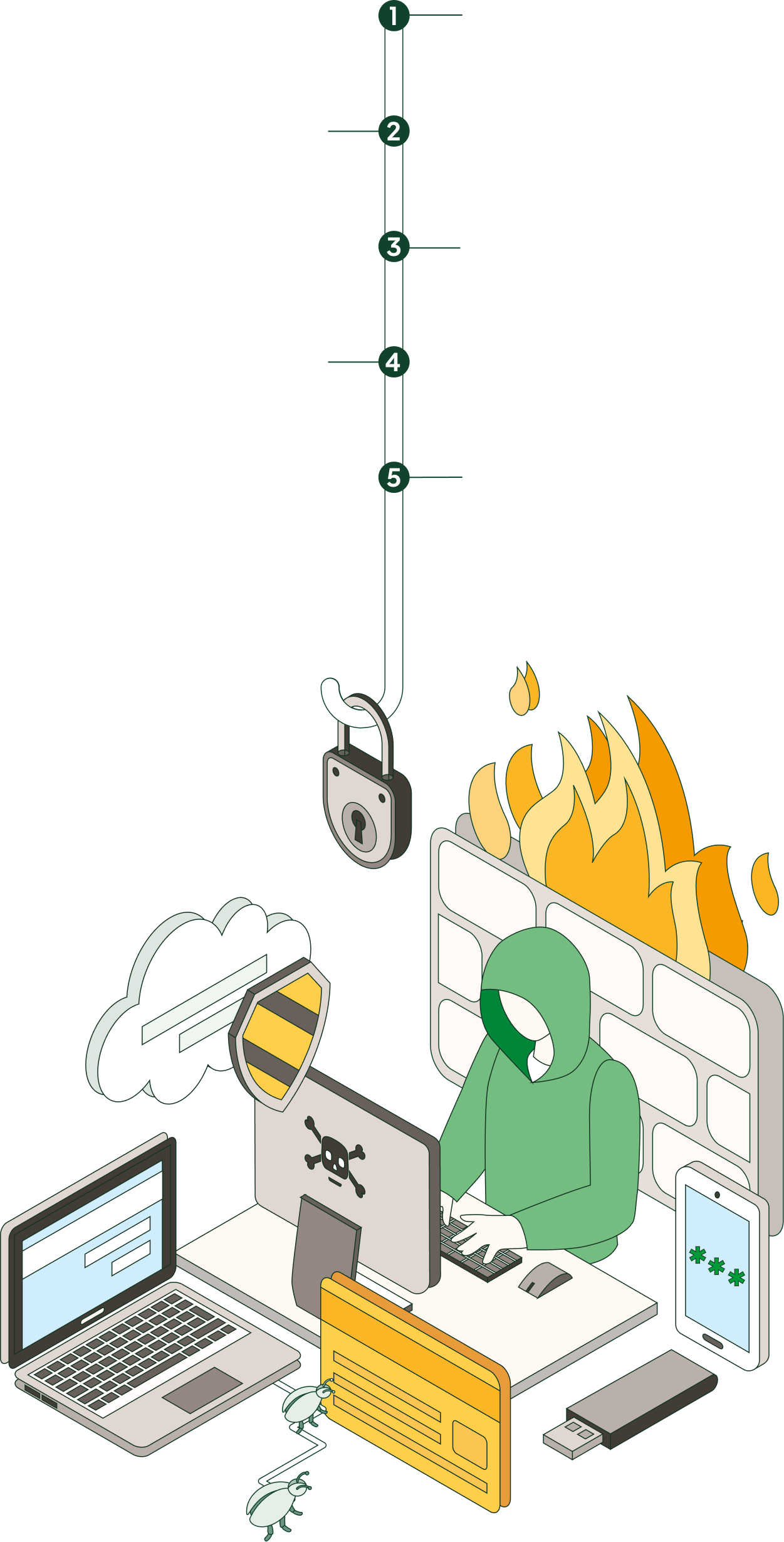
Have you ever heard of phishing? It is a type of cyberattack that is becoming more common. Cybercriminals use this technique to fraudulently defraud and obtain confidential information.
Phishing: a click makes the difference.
What is phishing?
Phishing consists of sending messages, either via email, SMS (named smishing), instant messaging or even social networks, in which cybercriminals mimic the identity of a known organisation to gain access to our most confidential information (passwords, bank details...) by encouraging you to click on a link that redirects you to a fake page.
Emails often include a link that leads the user to counterfeit websites. Once there, personal information is requested from the user and, believing the website is trustworthy, they provide it, falling into the hands of scammers (or phishers).
Phishing can also take place on web pages through advertising banners that encourage you to download an antivirus or any other program by filling in a form that requests personal data.
Phishing attacks are increasingly sophisticated and convincing and confuses users to compromise their own security. The worst thing about these cyber-attacks is that most of the time they infect your terminal — whether mobile or computer — without you noticing.
These cybercriminals use many excuses to capture our attention and redirect us to fraudulent websites that pretend to be legitimate: urgent updates, packages that you have not requested but need to collect as soon as possible, notices of a last payment, the bank asking you to change your password and so on...
But we can fight these cyberattacks. Monitoring a website or using a good antivirus are some of the most effective ways to win the battle against phishing. If you notice that a web page is fake — this happens when it doesn't start with https:// or doesn't have a closed padlock in the browser bar — our recommendation is to clear the browser's cache memory. This will allow you to remove any unwanted software.
History and evolution of phishing
The techniques and targets of phishing have evolved throughout its history. In the 1970s, its most important precedent emerged: a subculture around attacks via the telephone system. These early hackers were known as phreaks, a combination of the words "phone" and "freak". At a time when there were not many networked computers, phreaking became the first technique for defrauding users.
The creation of the term phishing was attributed to a well-known hacker in the mid-1990s, Khan C Smith. At the time, America Online (AOL) was the leading provider of internet access and hackers and hackers used it to carry out phishing attacks against users. Even when AOL adopted security measures, attackers resorted to other techniques such as posing as AOL employees to ask users to verify their accounts and provide billing information.
In the 2000s, cybercriminals developed a well-defined phishing strategy: they posed as a well-known global brand and targeted email addresses on a large scale. Any subject matter was valid to scam victims: bank account closure notices, charity campaigns, prizes... The aim was to usurp the identity of well-known, everyday brands in order to get their hands on victims' information and money. Phishing progressively turned its attention to exploiting online banking payment systems and social networks became an easy target for identity theft because of all the personal data registered on them.
In response to the security measures implemented over time and a certain maturity of the public towards the threat, phishing campaigns have become increasingly sophisticated. A scenario in which cybersecurity providers continue to innovate to respond to new challenges.
Process and type of information stolen through phishing
-
Forgery of a trusted person, organisation or company.
-
Sending messages by any means of communication.
-
A percentage of users trust the message and click on it.
-
Users access a fake website and enter their personal details.
-
Attacker obtains user's personal data and uses it for malicious purposes.
What kind of information does a phisher steal?
Personal data
- Mailing addresses
- ID document number
- Location and contact details
Financial information
- Credit card number
- Account number
- E-commerce information
Access credentials
- Social media
- Email accounts
- Online banking applications
SEE INFOGRAPHIC: Process and type of information stolen through phishing [PDF]
Types of phishing
IT security and privacy company IT Governance highlights the top five types of phishing today:
![]() Email Phishing
Email Phishing
Most phishing attacks are sent via email. The criminal registers a fake domain that mimics a real organisation and sends thousands of generic requests. The fake domain often has swapped characters, such as "r" and "n" next to each other to create "rn" instead of "m". In other cases, fraudsters create a unique domain that includes the legitimate organisation's name in the URL and images of the company or brand. As a general rule, you should check any email address that asks you to click on a link or download an attachment.
![]() Spear phishing
Spear phishing
This is a more sophisticated example of phishing. It refers to malicious emails sent to a specific person. Criminals practising this type of scam already have important information about the victim, such as their name, place of work, position...
![]() Whaling
Whaling
Whaling attacks are more targeted. They are phishing attacks in which cybercriminals impersonate high-ranking executives or other business leaders. While the end goal of whaling is the same as any other type of phishing attack, the technique is often much more subtle. Criminals take advantage of employees' willingness to follow their boss's instructions.
![]() Smishing and vishing
Smishing and vishing
In both smishing and vishing, the telephone replaces email as a method of communication. In smishing, criminals send text messages (the content of which is very similar to email phishing), and in vishing, they use a telephone conversation. One of the most common pretexts is messages from a supposed bank alerting of suspicious activity.
![]() Angler phishing
Angler phishing
Angler phishing is a new scam tactic whereby hackers impersonate care staff using social media platforms and accounts. Fake URLs, cloned websites, posts and tweets, and instant messaging can be used to persuade people to divulge sensitive information or download malware. Moreover, criminals can use the data that people voluntarily post on social networks to create highly targeted attacks.
How to avoid being a victim of this cyber attack?
All users run the risk of being victims of phishing. However, any public address will be more susceptible to attack. The first step is to avoid replying to any mail requesting personal or financial information. However, distinguishing a phishing message from one that is not may not be an easy task. That's why we are giving you are a few tips to help you avoid being tricked:
- Make sure the email address belongs to the sender.
- Pay attention to the tone of the content. Be suspicious if it requires urgent action or sounds too good to be true.
- Before clicking on a link from a website and giving your data check that the link is the real one.
- Use strong passwords: A strong password is one that combines uppercase letters, lowercase letters, numbers and symbols, and is at least 8 characters long.
- Do not leave sessions open. It is advisable to log out, disconnect or leave the service completely when you are not using it.
- Install an antivirus on all your devices and run recurrent scans.
SEE THE INFOGRAPHIC: Phising, a click makes the difference [PDF] External link, opens in new window.










